Cyber Security in Industrial Plant Environments
[1] Plant System Security
With the rapid development of IT and IoT technologies, closed Industrial Plant environments including ultilities and manufacturing have turned to open environments that are connected to various systems in order to improve productivity and make data more readily available. On the other hand, transitioning to an open environment makes external access possible, thus resulting in increased chances of security threats, such as cyber-attacks. Such cyber-attacks can cause serious damage to the Plant processes by suspending operation and so on. You need to take measures to mitigate the threats from these cyberattacks to achieve "Cyber Preservation" that ensures security and safety.
[2] Protecting Plant Systems from Cyber-attacks
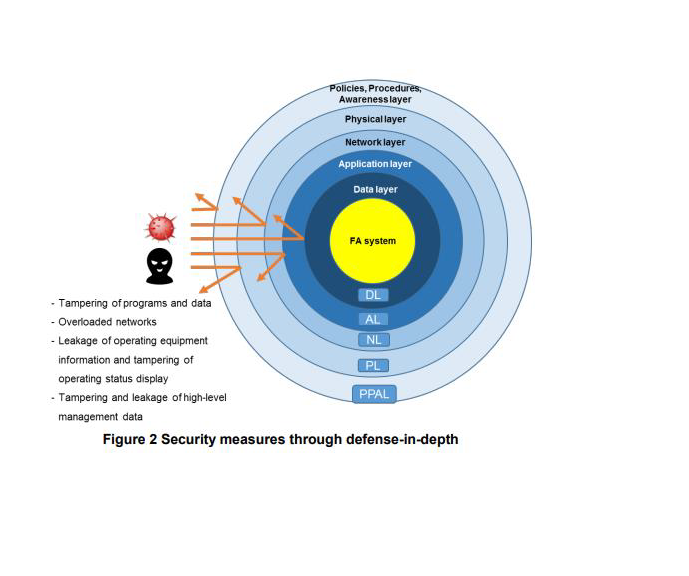
What is essential in security measures is to adopt defense-in-depth, in which measures are taken from different perspectives, such as data access, execution of applications, network access, use of equipment and facilities, and human work. These perspectives are defined as the data layer, application layer, network layer, physical layer, and policies, procedures, awareness layer. Use of defense-in-depth can increase the attack cost for attackers and also enhance the detection and defense abilities when a system is attacked, helping to reduce the impact of the attacks.
The security functionality of the programmable controller is one of the defense-in-depth measures. In addition, we ask customers to consider setting up firewalls, installing antivirus software in personal computers, and controlling the entrance into and exit from Plants to protect the systems from cyber-attacks.
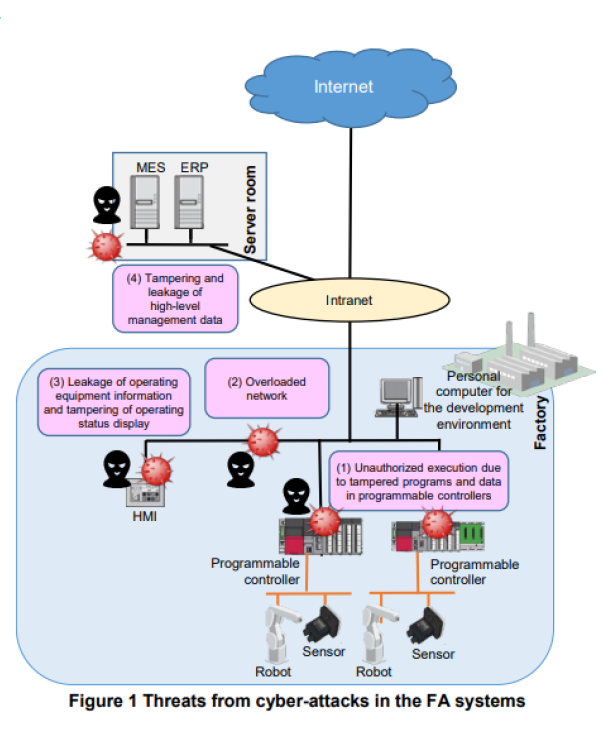
The following threats from cyber-attacks can occur:
(1) Unauthorized execution due to tampered programs and data in programmable controllers If programs and data (parameters and manufacturing data) on a programmable controller have been tampered with, the controller can be executed illegally, causing an error in control system.
(2) Overloaded network (DoS attack) A huge amount of process requests or data is sent to the target equipment over the network, resulting in increased traffic on the network and overloading of specific device nodes. As a result, the data transfer rate can become slow or data transfer can be interrupted.
Denial of Service attack: A type of attack in which the services and functions of computers (servers and equipment) and networks are made unavailable by overloading the computers and networks or abusing their vulnerabilities.
(3) Leakage of operating equipment information and tampering of operating status display. The operating information of each device that is collected and monitored by HMIs can be leaked outside and may be used as ammunition for attack. The operating statuses of the devices displayed on the HMIs can also be tampered with so that they are shown as errors, inducing administrators to shut down the system. Tampering and leakage of high-level management data Manufacturing data managed by high-level systems, such as MES servers, can be tampered with and may hinder proper manufacturing process management and quality control. The operating information of managed devices can be eavesdropped.
Defense-in-depth layer
The following are examples of measures for each defense-in-depth layer: -
Data layer (DL): Access control to programs and data through password authentication as well as program and data encryption and encipherment.
Application layer (AL): Installation of antivirus software in the equipment, user access control, and restricted program execution.
Network layer (NL): Traffic filtering by setting up firewalls, IP filter, and restricted remote access.
Physical layer (PL): Control over entrance into and exit from factories and offices, and locking of unused Ethernet and USB ports of devices.
Policies, Procedures, Awareness layer (PPAL): Preparation of policies and procedure documents and implementation of security training.
Defense-in-depth measures
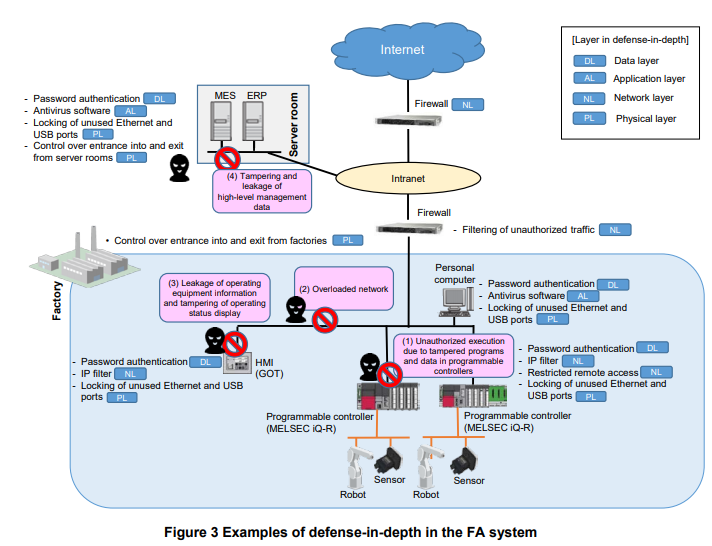
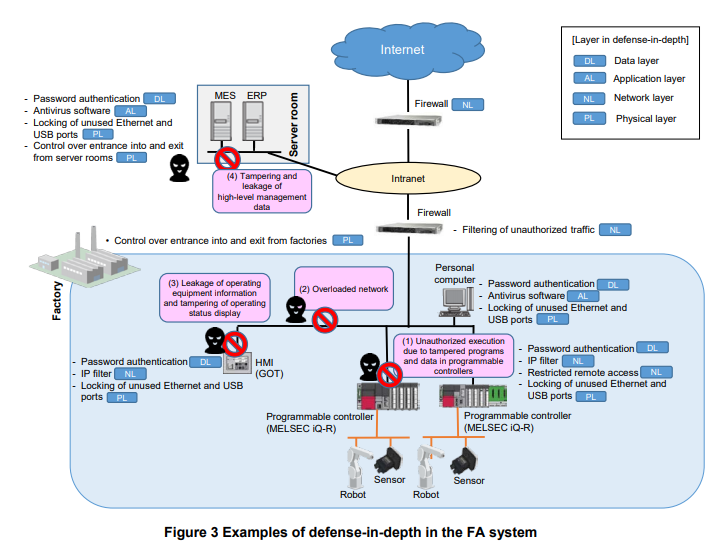
The following are defense-in-depth measures against the threats from cyber-attacks shown in Figure 1. (The preparation of policies and procedure documents and implementation of security training are common measures.)
(1) Unauthorized execution due to tampered programs and data in programmable controllers
- Use password authentication to restrict access to programs and data in the programmable controllers.
- Restrict network access by installing a firewall at the entrance of the plant network, activate the IP filter on the programmable controllers, and restrict remote access.
- Prevent programs and data from being tampered with by unauthorized threat Actors in the factories by using entrance and exit control into and from the factories (such as ID authentication and biometrics authentication) or locking unused Ethernet and USB ports on the programmable controllers and personal computers for development.
- Prevent programs in the programmable controllers from being tampered with by installing antivirus software, restricting login through password authentication, and encrypting the programs and data in the personal computers in the development environment for the programmable controllers.
(2) Overloaded network (DoS attack)
- Use firewalls to separate the Plant network from the intranet and to separate the intranet from the Internet, and restrict packet switching and the execution of applications.
- Activate the IP filter on devices to prevent packet switching from unauthorized IP addresses.
(3) Leakage of operating equipment information and tampering of operating status display
- Use password authentication when working with HMIs to prevent eavesdropping and tampering of operating information.
- Restrict network access by installing a firewall at the entrance of the network and activating the IP filter on HMIs.
- Prevent unauthorized threat Actors in Plants from eavesdropping by locking unused Ethernet and USB ports on HMIs.
(4) Tampering and leakage of high-level management data
- Restrict access to servers and data by installing antivirus software in MES and ERP servers and using password authentication.
- Install firewall to separate the Internet from the intranet and restrict network access to the servers.
- Take measures against unauthorized threat Actors by locking unused Ethernet and USB ports of servers and controlling the entrance into and exit from control rooms.
[3] Security Functions of Programmable Controllers
Here we introduce security functions provided by programmable controllers in relation to the security threats and measures described previously.
[3.1] This section provides information on a function that can be used to prevent the tampering and leakage of the programs and data in the programmable controllers
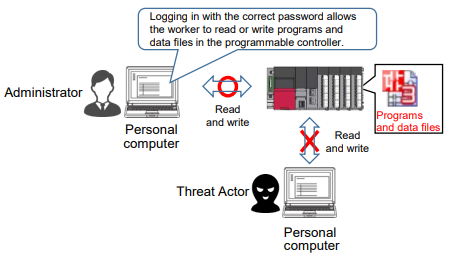
Preventing the programs and data files in the programmable controllers from being read or written illegally using password authentication A threat Actor can break the firewall and log in to a permanently installed personal computer. After that, the threat Actor can use an engineering tool to try to read or write programs or data files in the programmable controller illegally. To prevent this, you can use the "file password function," which prevents unauthorized reading or writing of files through password authentication. The password must be a string of eight characters or longer with three types or more of uppercase letters, lowercase letters, numbers, or special characters.
[3.2] This section provides information on a function that can be used to prevent unauthorized access to programmable controllers.
- Preventing access from external devices with unauthorized IP addresses
- Restricting remote access through password
(1). Preventing access from external devices with unauthorized IP addresses:-
A threat Actor can attempt to access programmable controllers by, for example, connecting a personal computer that they have brought in to the Ethernet or using a VPN illegally. To prevent this, you can use the "IP filter function," which prevents access from external devices with unauthorized IP addresses. Using the IP filter function, register only IP addresses of external devices that need to access the programmable controller directly (such as Control Maestro computers for the development environment) as access-allowed IP addresses on the programmable controller.
In addition to the security functions of the programmable controller, consider developing systems with defense-indepth measures, including having firewalls and installing antivirus software in Control Maestro computers.
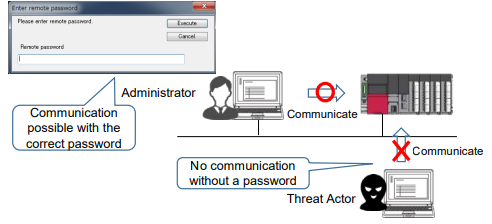
2). Restricting remote access through password:-
A threat Actor can attempt to make unauthorized communication with a programmable controller by using an engineering tool, SLMP, or FTP. To prevent this, you can use the "authentication function through password (remote password)" to connect remotely. Threat Actors who do not know the remote password cannot communicate through the engineering tool, SLMP, and FTP. The password must be a string of eight characters or longer with three types or more of uppercase letters, lowercase letters, numbers, or special characters.